Cybersecurity and personal data protection are critical issues across all industries, but network and communication technology providers play a fundamental role in mitigating and safeguarding users from rights violations and online threats. Therefore, True must rigorously pursue cybersecurity and personal data protection efforts, including the establishment of control measures, audits, and continuous improvement of management practices to meet standards consistently. This also involves building internal staff capabilities, educating business partners, collaborators, and continuously educating users and consumers. This ensures the creation of a secure digital environment for everyone, reducing legal, financial, and reputational risks for the Company.
GOVERNANCE AND STRUCTURE
One of True’s missions is to prioritize the management of personal data security in accordance with the Personal Data Protection Act B.E. 2562 (PDPA), as well as international guidelines and standards, such as the ISO 27001 Information Security Management Standard, covering all business units, including TrueMove H, True Online, TrueVisions, and True Digital.
The company has established the IT & Security Division and the Business Security Department under the Chief Technology and Information Security Officer (CTISO). It reports the results of Information Security and Cyber Security operations to the Risk, Cybersecurity, and Finance Committee, as well as to the management committee. Additionally, a Data Protection Division has been established to specifically manage personal data protection issues. Its main responsibility is to control the personal data protection processes in accordance with the company’s policies and the PDPA. This division operates under the Chief Corporate Affairs Officer Group and reports progress and operational results to the Corporate Governance and Sustainability Committee and the management committee.
In general, the scope duties and responsibilities of the Risk, Cybersecurity and Finance Committee in relation to cybersecurity and privacy protection include:
- Oversee risk policy framework and process for risk management of the Company, including all strategies, policies, rules and operational manuals to determine, evaluate, monitor and recommend cybersecurity risk, and data privacy risk to the Board of Directors;
- Regularly review the policy framework and process for cybersecurity and data privacy risk and propose recommendation for revision to the Board of Directors and determine risk metrics of the Company’s business;
- Promote and implement the policy by enhancing the level of cybersecurity risk awareness through the development of appropriate procedures and commitment of resources;
- Support the monitoring of risks including cybersecurity risk and data privacy risk across the Company and regularly report to the Board of Directors;
- Oversee and review the cybersecurity and privacy protection management and performance of the Company, including meeting regularly with management and commenting and giving opinions on any recommendations of management to the Board of Directors regarding long and short term strategies, expenses, etc.
- Monitor and evaluate the cybersecurity and privacy protection performance of the Company against the Company’s budget
Mr. Prasoon Sinha has served as Senior Vice President, Investment Management at Telenor Asia Pte Ltd, Singapore since July 2021. From 2017 to 2021, he served as the Deputy CEO and CFO of Wave Money, a Fintech joint venture of Telenor in Myanmar.
From 2014 to 2017, he was the Head of Dynamic Performance Management at Telenor ASA in Oslo, Norway. Prior to that, he held several key roles at Telenor India between 2008 and 2014 including Chief Financial Officer, Head of Business Strategy and Planning and Head of Technology Financial Planning.
He previously served as Head of IT Transformation and Technology Planning at Aircel Limited, India, experiencing Information technology and Cyber-security.
CYBERSECURITY & DATA PROTECTION POLICY
Cybersecurity and data protection are critical concerns globally, particularly in the telecommunications industry, which faces over 6 billion cyberattacks annually.
High ethical standards form the foundation of the Company’s business practices, applied to employees, business partners, and stakeholders across all regions and situations. Organizational integrity is seen as a key indicator of success and sustainable
growth.
At True, we are committed to upholding the highest standards of cybersecurity and data protection to safeguard customer, partner, and employee information. To reinforce our commitment to protecting data and maintaining a secure digital ecosystem, True has developed and implemented the True Information Security Policy, which provides a comprehensive framework for managing information security risks across our operations.
The policy outlines our strategic direction and operational approach to ensure business continuity, safeguard stakeholder trust, and comply with relevant legal and regulatory requirements. It covers a wide range of critical areas, including but not limited to:
- Ensuring the integrity, confidentiality, and availability of data and IT assets
- Establishing clear roles, responsibilities, and accountability for information security across all levels of the workforce
- Defining information security requirements for third parties, including suppliers and service providers
- Managing access control and protecting against unauthorized access, loss, or misuse of data
- Promoting information security awareness and training to build a culture of vigilance
- Supporting secure system development and changing management processes
- Monitoring, detecting, and responding to information security threats in a timely and effective manner
- Ensuring incident response procedures are in place to manage and mitigate potential breaches
- Conducting audits and reviews to assess compliance and identify areas for improvement
- Continuously improving information security systems through regular assessments and updates
This policy is reviewed regularly and integrated into True’s broader risk management and governance frameworks.
In addition, as part of our commitment to continuous improvement, True has appointed dedicated IT and Information Security personnel responsible for overseeing the performance and advancement of our security systems. Regular cross-functional meetings are conducted with relevant departments and management level to assess the status of IT operations and identify any security-related issues or opportunities for improvement. Through this structured engagement, key findings and proposed enhancements are escalated to management for timely review and decision-making.
IT & SECURITY STRUCTURE AND RESPONSIBLE PERSONNEL
The IT & Security Division and the Business Security Department both report to Chief Technology and Information Security Officer (CTISO). These units are responsible for overseeing data and cybersecurity operations and report their performance to various committees, including the Risk, Cybersecurity and Finance Committee, as well as the company’s Board of Directors.
The CTISO has the following duties and responsibilities:
- Establish procedures for controlling and auditing third parties and external agencies authorized to access the company’s data and assets, ensuring strict adherence to this policy.
- Regularly review the company’s policies and practices related to information and cybersecurity, assess risks, and ensure that high-risk issues are recorded in the company’s risk register.
Additionally, the Head of Security was appointed with the primary responsibility of ensuring that data and asset security operations align with company policies and providing performance progress updates, including reports on any policy violation incidents.
True has Personal Data Protection Policy designed in accordance with the PDPA framework, which is enforced rigorously within the Company, including subsidiaries, business partners and those appointed to act on behalf of the Company. One key aspect of the policy is defining the Company’s role as a “Data Controller,” which entails the authority to determine the purposes and methods of processing personal data arising from business operations. This is considered the duty and responsibility of the Company as the Data Controller, requiring various measures to ensure effective and appropriate data protection under PDPA principles and using customer data only for the purposes for which consent has been provided.
Additionally, a Data Protection Officer (DPO) is appointed, tasked with providing guidance to management, employees, and relevant individuals on risks and best practices regarding personal data processing. The DOP reports non-compliance and policy violations to the Company’s management and operates independently to review the use of personal data within the Company’s internal activities without interference.
The policy includes other important aspects in line with the PDPA, such as:
- Defining the responsibilities of employees or authorized personnel who access personal data, along with implementing controls and access limitations.
- Clearly defining the duration of data retention, usage, and destruction, as specified in customer consent agreements, and strictly adhering to these guidelines.
- Establishing procedures to control and audit partners and external entities authorized to access personal data from the Company, ensuring strict compliance with this policy.
- Making personal data protection a focal point in internal audits across all business operations, reporting audit findings to the Audit Committee, and taking immediate corrective actions upon discovering violations or policy breaches.
- Regularly reviewing policies, practices and assessing risks related to personal data, with high-risk issues being documented in the Company's risk register.
- Establishing data storage and maintaining records of customer personal data.
- Providing channels for complaints and reporting situations that may deviate from or violate policies and practices.
- Enhancing employee understanding and capabilities through communication, knowledge training, and awareness-building initiatives.
The Company assesses and reviews its personal data sharing processes and practices with internal entities and third parties annually, conducted by both internal and external auditors to ensure privacy policy compliance.
IT & SECURITY MANAGEMENT PROGRAM
To ensure the integrity, resilience, and continuous improvement of our cybersecurity infrastructure, True has developed a comprehensive IT system and audit framework aligned with international standards and industry best practices. This framework is designed not only to protect data and digital assets but also to strengthen stakeholder confidence through transparency and accountability.
Key elements of our IT system and testing/audit program include:
- Security Management Systems & Operational Procedures
True has established formal security management systems that integrate key components such as risk assessment, access control, data protection, and incident response. These are supported by:
- A regularly tested Business Continuity Plan (BCP) to ensure operational resilience
- This process clearly outlines roles, responsibilities, and communication channels to promptly escalate incidents to appropriate response teams and management, ensuring timely containment, investigation, and resolution of security events A defined escalation process for managing security incidents
- Clearly documented internal procedures, such as the “Information Security Incident Response Procedure” and “IT Risk Management Guidelines“
- These procedures provide step-by-step guidance for identifying, reporting, analyzing, and mitigating information security risks and incidents, supporting consistent and effective handling aligned with organizational policies and compliance requirements
- Certification: ISO/IEC 27001
- True has established a comprehensive cybersecurity and data protection framework aligned with international standards to safeguard sensitive information and maintain digital resilience.
- The Company achieved ISO/IEC 27001:2022 certification, reflecting full compliance across all operations. In 2024, True successfully upgraded its ISO 27001 certification from 2013 to the 2022 version, covering all business operations and ensuring 100% compliance.
3. Data Governance & Operational Safeguards
- Data Classification & User Access Review:
- Annually conducted to categorize data based on sensitivity and manage access rights accordingly.
- Data Loss Prevention (DLP):
- Annually Fully implemented DLP systems to prevent unauthorized data leaks.
- Disaster Recovery Plan (DRP):
- DRP and Incident Response Plans are reviewed semi-annually for critical systems.
4. Penetration Testing, Vulnerability Scanning & Threat Response
- Penetration and Vulnerability Testing:
- Includes simulated attacks and abnormal behavior detection using advanced analytics for real-time threat prevention.
- Performed annually to assess over 2,000 servers for system weaknesses and strengthen cyber defenses.
- Vulnerability Analysis & Threat Management
- A regular vulnerability assessments and threat analysis activities is conducted to identify potential system weaknesses.
5. Risk Assessment, Audit, and Verification
- Internal and External Audits: Conducted annually to assess systems that handle personal data, ensuring compliance with regulatory and security requirements.
- Risk Assessment: Regular evaluations of cyber and IT-related risks using both in-house and third-party experts.
- Abnormal Incident Monitoring: In 2024, 15,119 abnormal incidents were detected and successfully prevented.
- No reported incidents: True reported zero cases of data loss, destruction, or theft in 2024, with no revenue impact from such events.
6. Employee Awareness & Capacity Building
- Cybersecurity Awareness Training: 100% of employees participated in both online and on-site training sessions to promote a security-first mindset.
- Security Personnel & Governance: A dedicated cybersecurity team and responsible officers—including the appointed Data Protection Officer (DPO)—oversee policy implementation, threat monitoring, and issue escalation to management.
2024 PERFORMANCE
As the exponential increase in customer data usage and online transactions has significantly heightened digital inter-dependencies, the Company is continuously enhancing and expanding services and digital platform to serve this growing demand. However, the rise in complex and frequent cyberattacks, utilizing advanced techniques including malware, ransomware, phishing and other means to obtaining unauthorized access to our telecom networks and systems has elevated cybersecurity risks. This necessitates the implementation of more advanced defense architectures to protect our telecom networks and systems. Cybersecurity failures cause data loss, sensitive personal data leakage as well as equipment failures and network interruption, could result in business disruption, financial loss, reputation damage and legal liability.
To cope with Cybersecurity threats, True has mitigation actions in terms of:
Infrastructure And Technologies
- Continual improvement of network security, data security system, and digital infrastructure according to ISO and CIS standard.
- Establish and continuously enhance the Security Operation Center (SOC) while upgrading to the certified ISO/IEC 27001:2022 standard
- Implement Security Orchestration Automation Response and apply advanced Security Operation Center (SOC) threat modelling to improve identification of cybersecurity threats, prioritize, and perform risk mitigation as well as to develop Incident Response (IR) procedures
- for handling incident types such as malware, business email compromise, phishing, and Advanced Persistent Threat (APT), etc.
- Continuous Monitoring and Improvement to detect and respond to cybersecurity threats in real-time and adopt of Machine Learning for incident detection and Threat Intelligence Service as a threat hunting to detect emerging threats in the wild. Regularly review and update security measures to adapt to evolving threats and technologies.
- Automated security checks: Vulnerability Assessment scan is performed on internal (monthly) and external systems (weekly), having Penetration testing on timely basis, all findings to be tracked and mitigated in a timeframe according to its risk level.
- Secure data protection for sensitive/personal data at both in-transit and at-rest data by having access control, authentication mechanism and encryption of data. Implement rigorous cyber hygiene processes to ensure comprehensive protection and resilience against evolving cybersecurity threats.
CAPACITY AND CULTURE
- Capacity building for IT workforce about evolving cybersecurity, including advanced technologies such as AI, NFT, and crypto currency payment.
- Cybersecurity architecture forum and Cybersecurity Ambassador were set up to make sure all employees adhere to the policies and practices and comply with the Personal Data Protection Act and other related laws. Employees can consult Data & Security Governance and Data Privacy Center team.
- Continue building a culture for cybersecurity through internal communication media, cybersecurity hub, online and onsite training in both intermediate and advance journey projects to staff and managements.
2024 Incident cases
- Abnormal Incident Monitoring: In 2024, 15,119 abnormal incidents were detected and successfully prevented.
- No reported incidents: True reported zero cases of data loss, destruction, or theft in 2024, with no revenue impact from such events.
PERSONAL DATA PROTECTION POLICY
True has Personal Data Protection Policy designed in accordance with the PDPA framework, which is enforced rigorously within the Company, including subsidiaries, business partners and those appointed to act on behalf of the Company. One key aspect of the policy is defining the Company’s role as a “Data Controller,” which entails the authority to determine the purposes and methods of processing personal data arising from business operations. This is considered the duty and responsibility of the Company as the Data Controller, requiring various measures to ensure effective and appropriate data protection under PDPA principles and using customer data only for the purposes for which consent has been provided.
Additionally, a Data Protection Officer (DPO) is appointed, tasked with providing guidance to management, employees, and relevant individuals on risks and best practices regarding personal data processing. The DPO reports non-compliance and policy violations to the Company’s management and operates independently to review the use of personal data within the Company’s internal activities without interference.
The policy includes other important aspects in line with the PDPA, such as:
- Defining the responsibilities of employees or authorized personnel who access personal data, along with implementing controls and access limitations.
- Clearly defining the duration of data retention, usage, and destruction, as specified in customer consent agreements, and strictly adhering to these guidelines.
- Establishing procedures to control and audit partners and external entities authorized to access personal data from the Company, ensuring strict compliance with this policy.
- Making personal data protection a focal point in internal audits across all business operations, reporting audit findings to the Audit Committee, and taking immediate corrective actions upon discovering violations or policy breaches.
- Regularly reviewing policies, practices and assessing risks related to personal data, with high-risk issues being documented in the Company’s risk register.
- Establishing data storage and maintaining records of customer personal data.
- The Company will only use personal data for marketing, promotional, or analytical purposes with the customer’s prior consent.
- Customers have the right to withdraw their consent for specific data processing at any time.
- Enhancing employee understanding and capabilities through communication, knowledge training, and awareness-building initiatives.
- Providing channels for complaints and reporting situations that may deviate from or violate policies and practices.
- Punitive measures in case of privacy policy violation by any employees, suppliers or business partners, the company will consider taking punitive measures according to our regulations and/or taking appropriate legal action.
The Company assesses and reviews its personal data sharing processes and practices with internal entities and third parties annually, conducted by both internal and external auditors to ensure privacy policy compliance.
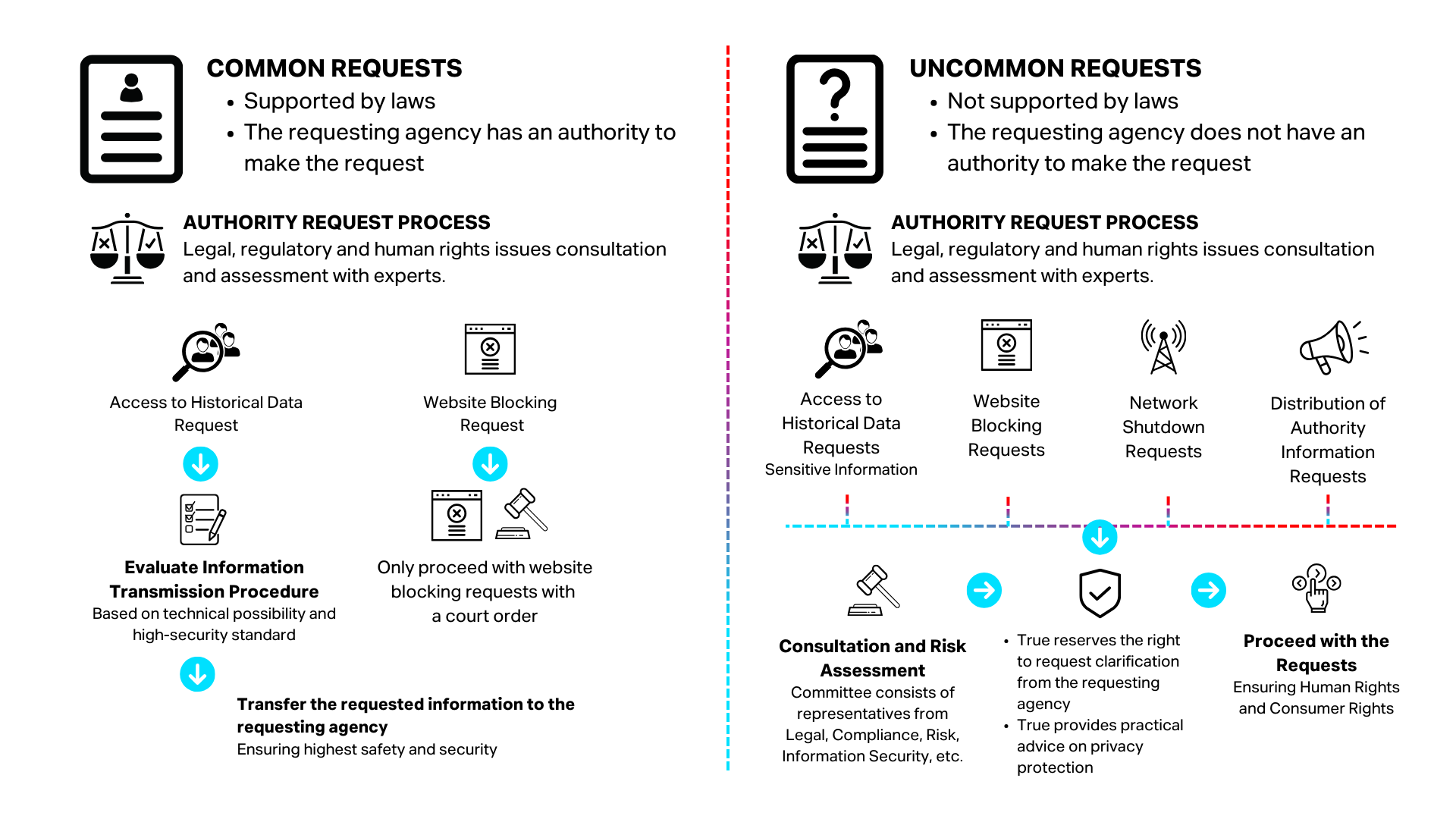
HANDLING AUTHORITY REQUESTS FOR DATA DISCLOSURE
-
Transparency:
Assessing whether the request is made by a lawful authority and complies with the consent provided by the customers. -
Necessity:
Evaluating the urgency and necessity of the data request, ensuring it compliments the proposed solution from the requestor.
-
Proportionality:
Determining whether the requested data volume is appropriate for the intended purpose.
-
Human Rights:
Ensuring compliance with human rights principles and assessing whether any misuse of data requires remedial actions and processes.
COMPLIANT REPORTING AND HANDLING, REMEDIATION AND PUNISHMENT
True provides channels for employees, customers, partners, and the general public to report complaints and situations that may violate or deviate from the company’s policies and practices regarding data security and customer data protection. These reports are handled through processes involving assessment, investigation, inquiry, mediation, and penalties for violations of the company’s Code of Conduct. The Compliance & Ethics Department oversees these processes. In the event of personal data breaches, the company has effective legal remedies in accordance with PDPA criteria and methods. If violations that contravene policies are identified, legal penalties will be considered. Additionally, if company employees violate policies and practices, they will face disciplinary action in accordance with the Code of Conduct and may be subject to legal penalties as prescribed by law.
RESPONSIBLE ARTIFICIAL INTELLIGENCE (RAI)
True’s AI Charter
AI usage is comprising of 3 aspects:
1. Setting ethical goals,
2. Ensuring all employees have technology knowledge for the transition to a Data-First and AI-First organization, and
3. Prioritizing ethical principles in AI usage.
True has already drawn up “True’s AI Charter” to lay down AI governance guidelines for its internal use. This charter prescribes four following guidelines:
1. Good Intent: AI should only be used for the benefit of customers and not pose a threat to others.
2. Fairness and Bias Mitigation: AI must not lead to results that reflect discriminatory practices.
3. Data Privacy and AI Functionality: The outcomes of AI usage should adhere to privacy principles, respecting the level of access customers provide.
4. Transparency: Despite the complexity of AI operations, the results of AI processing must be explainable, considering “rights” where consumers are paramount.
True Corporation Reaffirms Its Position as a Thai Tech Company, Emphasizing That No Matter How Intelligent AI Becomes, It Must Be Used Ethically, with Respect for Human Rights, Transparency, and Accountability
In today’s fast-paced digital world powered by technology, Artificial Intelligence (AI) is rapidly playing a significant role in both business and society. With processing capabilities over 200,000 times faster than the human brain, AI can diagnose diseases with over 95% accuracy and support sustainability efforts, such as addressing climate change. However, on the other hand, AI can be a “double-edged sword.” Without ethical frameworks, it can lead to privacy violations, the spread of misinformation, and increased inequality due to biases hidden within the data used to train AI. As a technology organization that recognizes the importance of ethical AI development, True Corporation reiterates its commitment to supporting the ethical use of AI.
AI is a technology closely linked to personal data protection. As an organization committed to good governance principles, True places great importance on safeguarding customers’ personal data, which is another dimension of respecting human rights in the digital era. The company adheres to the principle of “Privacy and Security by Design,” ensuring that customer privacy is protected from the very beginning of the design process. True also evaluates the impact of every service involving personal data, especially those resulting from the use of AI technology.
- True adheres to four pillars for ethical AI development, which are:
2. True Corporation is committed to the responsible development and use of Artificial Intelligence (AI), guided by four key principles:
3. Transparency – Providing clear and explainable information about AI processes and decision-making, based on factual evidence.
4. Respect for Human Rights – Upholding the dignity, privacy, and freedom of every individual, ensuring that AI does not harm humans.
5. Fairness and Inclusion – Ensuring that AI delivers equitable outcomes, free from bias and discrimination against any individual.
6. Human-Centered Design – Prioritizing the well-being, safety, and accessibility of all users.
True Corporation is the first organization in Thailand to implement a Responsible AI (RAI) policy in accordance with the GSMA’s framework at the organizational level. The company has integrated the RAI Framework into its internal processes and established guidelines for performance evaluation aligned with international standards. This ensures the safe, fair, and sustainable use of AI, in line with global best practices.
True iService has achieved remarkable success, with 5.2 million monthly active users being attracted to the app. Between 2021 and 2022, the app experienced a high growth rate of 12%. The primary focus of True iService is the development of automated self-services that cater to both before and after-sale needs. Users can conveniently perform tasks such as bill payment, registration of new phone numbers, subscription to mobile and fibered internet plans, and troubleshooting for basic issues.






